Consonants
the grkvlt irregular publishing mechanism - enterprise java, web development, information security, statistics and probability, gambling, book reviews and technology discussion, together at last!
27/05/2015
What Really Happened to the Search Results?
What has happened is that using Google to search for the phrase what happened to the dinosaurs triggered a match on a book with a similar title: What Really Happened to the Dinosaurs by Ken Ham. His crime is to be a creationist. Can you believe it? Those sneaky Christians have gone and adjusted Google's search algorithm, so that when you search for the title of a book, you get back a bunch of information about the book. Think of the children!
Oh, wait. No. There's definitely a lack of critical thinking going on here somewhere, though. What's worse is all the oh-so-clever geniuses leaving 'feedback' about this, explaing how the result is incorrect because science! and similar. They semm to also have failed to notice this response to their submissions: Note: Your feedback won't directly influence the ranking of any single page. Probably because they are gleefully posting about how they have 'corrected' Google. They also appear to believe that despite this, the invisible hand of Google has listened to them, and removed the ofensive result, rather than what has actually happened - all the recent posts about the 'controversy' are weighted higher by the search algorithm, because they are more recent pages...
Grrr. If there's one thing I hate it's idiots like this who believe they are more intelligent that they are (see also Dunning-Kruger effect) and are blessed with super-rational skepticism that makes them infallibly right, unlike those poor benighted religionists. There's a time and a place for making fun of people who support flimsy beliefs with pretend science, and this is not it.
07/08/2012
Google TFA Security Issue
The following note describes a (serious) security vulnerability with Google accounts two-factor authentication, which I believe enabled complete TFA bypass and would therefore lead to full account access. I have raised this with Google, but it is a 'Known Issue' and no action is being taken, so they have no constraints on publication. I understand their security versus usability tradeoff, so this is mostly an exercise in full disclosure.
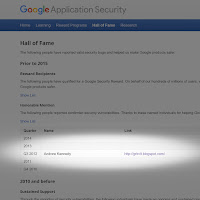
Since there was no bounty awarded, the issue was only recorded on the Honorable Mention list for Q3 2012. It can be found in the Prior to 2015 section of the Google Security Hall of Fame archive. If you want to verify that my name really is there you will need to click on the Show List link, and then search for Kennedy. The screenshot to the left is an edited copy of this page, created to highlight my entry, but there are a lot of other honourable mentions, so follow the link to see everything in context...
UPDATED 2013-02-25
The same issue has been discovered and blogged about by Duo Security researcher Adam Goodman - Bypassing Google’s Two-Factor Authentication and Hacker News discussion.
Issue
It is possible to bypass and disable two-factor authentication and re-enable it with a different Android device and phone number without ever knowing the account password or having access to an authorised authenticator or phone number.
Discovery
I enabled two-factor authentication or two-step verification [1] on my Google account last year, using an Android phone connected to an Orange PAYG SIM to generate the validation codes. In the process of moving flat, I lost this phone and also mislaid my printed set of backup codes. This meant that I was unable to authenticate myself to any of the Google account services over HTTP/HTTPS, as after accepting my password they all required the extra TFA code. These included the account and profile settings page, Google+, Blogger and other Google web properties such as YouTube.
In fact, the only Google services I could access were those for which I had an application-specific sixteen character password [2] already generated, and it was not possible to generate any further such passwords. Additionally, these passwords are not sufficient to log into any of the Google web sites, and attempts using them are rejected. The only approved way to disable TFA and regain access to Google sites was to go through the account recovery process [3] which requires detailed knowledge of the history of the account. Even as the owner of the account, I was unable to provide enough correct answers to satisfy Google support and regain access although I tried several times.
Using the vulnerability below I discovered that I was able to bypass the normal restrictions and re-configure the account security settings to give me access to my account again, and register my new phone and device instead.
Requirements
The following are required to gain access to a two-factor authentication protected account. Note that the main password is not needed, nor is access to any of the configured authentication devices or phone numbers.
- Any application specific password for the Google account (This can usually be obtained by examining the configuration files for an application using the password, or looking in the 'Keychain' on OSX or other operating system equivalent)
- Android 3.2.2 device (As tested, other versions may also work)
Process
The following process will enable full access to, and control of any Google account protected by two-factor authentication. I have tested this using my own Google account.
- Add the Google account to the Android device, giving the application-specific password as the credential
- Ensure 'Google automatic sign in' is enabled for the Android browser
- Access Google's homepage using the browser
- Click on 'account settings' or other link which requires authentication with Google
- The browser will automatically authenticate the account you will be logged in as the chosen account
- It is now possible to change all two-factor authentication settings, either disabling it completely or changing the configured device and phone numbers used to generate codes
Conclusion
This is a serious flaw, since users assume that their accounts cannot be compromised unless an attacker obtains the device used for authentication, or gains control of their authorised phone number, neither of which is required for this attack.
It is possible to log into an account protected by two-factor or two-step authentication without ever invoking this process or having access to the authorised device or phone. This bypasses all protections that are assumed to be provided by the service, allowing an attacker in possession of an application specific password to gain complete control over a two-factor protected account which the user assumes is safe.
References
23/09/2011
Reboot
I have recently started working at a new company, a cloud technology start-up based at Edinburgh University. Cloudsoft produce Monterey, a middleware framework for application mobility across various cloud infrastructure providers. I am developing the latest version of this, on which more later. It is a great environment to work in, with really smart colleagues and lots of challenges that keep me thinking. There are also the obvious benefits of being based in the University, such as very fast Internet and free access to academic journals.
Due to the scope of my work, I have found myself learning a lot of interesting new things. These range from picking up new languages (Groovy), libraries and APIs (jclouds, AWS, Seam CDI), applications (Redis, Karaf, Chef, Infinispan) as well as technologies (OSGi, PaaS). I am also working on open source projects during 20% of my time, which will mostly involve Qpid but I have also been investigating jclouds and elasticsearch. I hope to be able to write more about many of these topics.
01/08/2010
Silly, Mischievous Fools and Rogues
There would be widespread opposition to such a regulation as inconsistent with English liberty. Our tradition is that while orders issued by the duly constituted authority must be obeyed, every civilian is at liberty to show, if he can, that such orders are silly or mischievous and the duly constituted authorities are composed of fools or rogues [...] Accordingly we do not regard activities which are designed to bring the duly constituted authorities into contempt as necessarily subversive; they are only subversive if they are calculated to incite persons to disobey the law, or to change the Government by unconstitutional means. This doctrine gives, of course, great and indeed dangerous liberty to persons who desire revolution, or desire to impede the war effort [...] but the readiness to take this risk is the cardinal distinction between democracy and totalitarianism.
Sir Alexander Maxwell
06 September 1940
13/02/2010
LEGO Games 3835 Robo Champ
This is an excellent game, both conceptually and in actual execution. It consists of LEGO pieces, and instructions to build three brightly coloured, cartoon style robots and one die. All the robot LEGO pieces provided are standard shapes and sizes, as found in any conventional LEGO set, and there are 118 separate pieces in total. The only custom part is the die, which accepts 2x2 tiles on each face (or combinations of two 2x1 or four 1x1 tiles) so you can re-use parts or build extra robots if desired. The robots themselves are fairly simple to build and great to look at and play with once built - in fact the set would be worth it just as a three-robot kit, I feel! Once built, the robot arms, legs and heads are detatchable by design, and this is an essential feature of the game...
There is a contest at the robot factory. The first to build a robot with all the correct colour parts will win this year’s trophy and be named the Robo Champ. If someone takes a part you need you may have to steal it back to achieve victory. A fast and fun game to play again and again for 2 to 3 players. Game play approximately 10-15 minutes.
Gameplay is quite straightforward, with the amusing back-story above presented in the instructions. Players take turns rolling the die and each get to pick, swap or steal an appropriately coloured robot part depending on the colour shown. In line with the spirit of LEGO, the rules are malleable, and it is suggested that players and families develop their own sets. I felt that the initial set of rules was complex enough to provide a fun game, but still easy to learn. The first game I played took around ten to fifteen minutes, just as suggested on the box, which included the learning time. Of course it also took some time beforehand to build the robot pieces involved, which will depend on your individual LEGO skills.
One caveat for this set is based on my experience with the recipient of the set I purchased, my young nephew. He is slightly younger than the suggested minimum of six years old, but has very readily grasped the idea behind building LEGO models from their instruction sheets, and loves robots of all kinds! He found it hard to grasp that his beloved new robots had to be taken to pieces after he built them so carefully, and also had difficulty accepting that he might not be able to re-build the robot with the correct parts. I think that older children would be able to understand this aspect of co-operative gameplay automatically, but it is a point to note if buying this for younger children. Also, the next time he plays, he will not have just built the new robots, so will be less apprehensive about their impending destruction.
There are several other LEGO game sets which intrigue me, such as Creationary and Lunar Command. i think this is a great idea from LEGO, and hope they continue the theme. Sadly, some sets, like Knight's Kingdom Chess Set are no longer available, but i think a quick look on eBay would probably net a copy.
LEGO® is a trademark of the LEGO Group of companies which does not sponsor, authorize or endorse this site.
04/02/2010
Brain Overflow
Anyway, the creators have spun off the software behind it as a stand-alone product for community question-and-answer sites as StackExchange. They sell consultancy and services as well as hosted versions of the software as white-label sites, and give away free access for non-commercial usage. It's a nice business model which I'd love to copy with my own software...
While looking at some of these associated sites, I discovered Math Overflow, which makes Andrew feel stupid.. This is chock full of people asking about non-trivial isomorphisms, homologous cauchy integral groups over non-integral fields, and getting intelligent answers! Of course, there's also lots of homework questions, and potentially unanswerable stuff in there too. I really like some of the philosophical discussions that pop up, as well as the more basic questions which are good at reminding me how much of my education I've forgotten due to alcohol and time...
The whole point of this post is that I found this amazing video, which is a sphere being turned inside-out in the most awesome way possible, with a little help from Pixar and the University of Minnesota. The frame shown is above is just part of the transformation, which is very clearly explained. The whole video is just over 20 minutes long, and I suggest you watch it all the way through, as it's pretty cool (and probably expensive, counting the number of grants that funded it...) animation for 1994.
18/04/2009
Working Standards
one of the only problems so far is the continuous integration system, which is set up with a very strict set of checkstyle and PMD rules for code quality. i'm all in favour of managing code quality as an automated process and continuous integration with these tools is a Good Thing, but i keep falling foul of some of the rules, in particular the checks for multiple return statements in one method, to enforce single exit points. i believe writing methods with guard clauses up front is the most readable and elegant way of expressing certain types of logic, and apparently martin fowler agrees (see his refactoring book) with me. the following discussion on stackoverflow is relevant, too. also, there are strict rules on long variable names, which keep me from naming things like constraintDefinition or workflowInstance although i do agree with the restriction on short (less than four characters) names.
i'm (really) going to try and make more of an effort to keep this blog updated more frequently, since it's over a year since i last posted ;)
16/03/2008
greenock central
sunset over greenock central station taken with panorama setting by stitching three landscape frames together using a sony ericsson camera phone.
29/02/2008
images from outer space...
I uploaded the images from Bruce to a Flickr set, and tagged them with a note indicating the asteroid's location, since it's very faint (magnitude 16.6 in these images). Also, to see more details, including the IAU discovery details and citation, as well as confusing orbital ephemeris and data, I have updated the Wikipedia article. This contains the image you can see here, which is a composite of the LONEOS frames, saved as an animated GIF to show the motion across the fixed stellar background. I really can't explain how much I appreciate the fact that Ted named this object after Malcolm, so I'd like to publicly thank him anyway.
02/10/2007
coming home present
the problem is, of course, whether to be happy that biggles likes me enough to give me his dead mice, *OR* to be worried that there is (was) a mouse (or mice) in my flat... maybe it's time to board up the hole in the bathroom wall before it gets colder?